Exclusive: They Spy with Their Little Eye
The Five Eyes, a part of what the NSA calls internally its “global network,” have their dirty fingerprints all over the latest spying scandal engulfing New Zealand, writes exiled Kiwi journalist and activist Suzie Dawson.
NZ Spy Scandal: Elephants In The Room;
US Used NZ Spies to Spy on Third Countries,
Including France; US Army Ready for Unrest
 I’ve spent six years alternately begging major NZ journalists to investigate state-sponsored spying on activists including me, and, out of sheer necessity, reporting extensively on it myself from within the vacuum created by their inaction. So it is somewhat bemusing to now observe the belated unfolding of what ex-Member of Parliament and Greenpeace NZ Executive Director Russel Norman is describing as New Zealand’s “Watergate moment“.
I’ve spent six years alternately begging major NZ journalists to investigate state-sponsored spying on activists including me, and, out of sheer necessity, reporting extensively on it myself from within the vacuum created by their inaction. So it is somewhat bemusing to now observe the belated unfolding of what ex-Member of Parliament and Greenpeace NZ Executive Director Russel Norman is describing as New Zealand’s “Watergate moment“.
In the wake of the bombshell release of a State Services Commission report into the affair, Norman wrote: “My key takeaway is that under the previous government, no one was safe from being spied on if they disagreed with government policy.”
This is a remarkable statement from Norman, who once sat on the very government committee tasked with oversight of New Zealand’s intelligence agencies. The futility of that lofty position was reflected in my 2014 piece “Glenn Greenwald and the Irrelevance of Electoral Politics“ which quoted Greenwald, who won the Pulitzer Prize for his reporting on NSA whistleblower Edward Snowden’s leaks, saying of Norman:
“You had the Green Party leader here in New Zealand say in an interview that I watched that he was on the committee that oversees the GCSB [ Government Communications Security Bureau – NZ’s electronic spying agency] and yet he learned far more about what the agency does by reading our stories than he did in briefings. They really have insulated themselves from the political process and have a lot of tools to ensure that they continue to grow and their power is never questioned.”
The sands are shifting: Over a dozen government agencies including the New Zealand Police are revealed to have been engaging private intelligence firms such as the notorious Thompson and Clark Investigations Limited to spy on New Zealand citizens engaged in issue-based democratic dissent, activism in general, or who were deemed to present an economic or political ‘risk’ to the bureaucracy or the private sector in New Zealand.
The media response has predictably walked the safest line – focusing on the egregiousness of the victimisation of the least politically involved targets such as earthquake insurance claimants and child abuse survivors, and honing in on the very bottom rungs of the culpability ladder. They are as yet failing to confront the international and geopolitical foundations that lie under the surface of outsourced state-sponsored spying in New Zealand.
The truth is that the roots of the issue go far deeper than subcontractors like Thompson and Clark. The chain of complicity and collusion leads far beyond the head of any department or agency, including the Head of the State Services Commission. It goes beyond even the Beehive (housing the cabinet rooms), the New Zealand Parliament and the Office of the Prime Minister.
At its core, this scandal is a reflection of fundamental flaws in the very fabric of intelligence gathering practices in New Zealand, its infrastructure and network – where the collected data flows, whom the collection of that data serves and to which masters our intelligence services ultimately answer.
I agree with Russel Norman that this could be New Zealand’s Watergate moment. But there are major aspects which to this day, have not been meaningfully addressed, if at all, by the New Zealand media – and of which the vast majority of the New Zealand public remain unaware, to their detriment.
Firstly: where is the data that is being collected by these spies really going? Secondly: who is directing New Zealand’s human intelligence assets and apparatus in foreign intelligence operations? And thirdly: what is the impact for Kiwis who unwittingly cross paths with our spy agencies in a country where the legal definition of ‘threat to national security’ has been removed?
1. ICWatch New Zealand
When the savant-like and (then) still teenaged M.C. McGrath, founder of the Transparency Toolkit, received an email from a member of the U.S. intelligence community threatening, “I promise that I will kill everyone involved in your website. There is nowhere on this earth that you will be able to hide from me,” he took the threat seriously. He had good reason to. His ICWatch initiative was using open source data to expose specific players, contracts and commercial relationships in the global intelligence community.
McGrath had discovered almost by accident that secret programs and projects, which would usually be hidden from public scrutiny, were often bragged about on the curriculum vitaes of current and ex-service members posted on LinkedIn. By pooling the publicly available data contained within their CV’s, he was able to shine light on many covert programs that we otherwise may not have ever known existed. Within the year he would resettle in Berlin, living in exile and his project rehoused at WikiLeaks. “Murderous spooks drive journalistic project to WikiLeaks” read the headline of WikiLeaks’ press release announcing their acquisition of ICWatch.
To my knowledge, no member of the New Zealand media has ever thought to peruse the ICWatch database to examine the extent of New Zealand’s involvement in that integrated “global network”, as the NSA so eloquently calls it. Or more appropriately, “the Total Force” referenced by ex-Secretary of Defence Donald Rumsfeld, when he redefined the term at a key moment post 9/11.
Jeremy Scahill, author of the fantastic read “Blackwater: The Rise of the World’s Most Powerful Mercenary Army” described Rumsfeld’s policy as being what “would become known as the Rumsfeld Doctrine, where you use high technology, small footprint forces and an increased and accelerated use of private contractors in fighting the wars.” (The ‘Total Force’ wasn’t just used to encapsulate these civilian contractors but also to indemnify them from prosecution or civil liability.)
The American adoption of large numbers of private contractors into their military has helped to stretch their tentacles deep into the South Pacific. It turns out that little old New Zealand is so in bed with this for-profit global surveillance network as to account for several hundred references that appear in ICWatch.
A study of the fine print on each search result reveals multiple intriguing tidbits: a reference to U.S. Army personnel being stationed in New Zealand. Another is to a New Zealand military liaison officer being stationed at Fort Meade in Maryland, a major U.S. military base and home of the NSA. (The existence of these liaison positions was revealed some years back however it is interesting to ponder what files may have crossed that desk in recent years.)
By far the most fascinating reference to New Zealand that I have found in ICWatch so far is to a U.S. Army intelligence officer who claims to have integrated “Czech, British, New Zealand and Jordanian intelligence into the Brigade’s CI/HUMINT enterprise”:
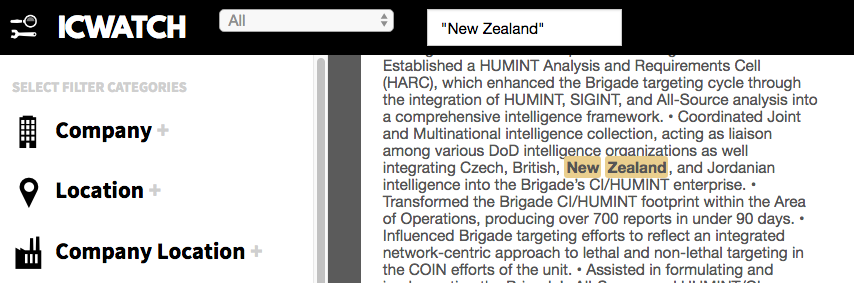
The above revelation that New Zealand’s Confidential Informant and Human Intelligence information and/or operations have been integrated into the U.S. intelligence databases and network is significant. It suggests that rather than sharing intelligence on a case by case basis, our spies are in fact supplying information wholesale and operating as a component of U.S. intelligence forces.
At the 2014 ‘Moment of Truth’ event in Auckland, Edward Snowden spoke of having direct access to “full-take” signals intelligence information from New Zealand while working as an NSA contractor. All of it, directly from the pipe. He said that in order to access that information, he merely had to tick a check box which said “New Zealand”.
The discovery that the products of our electronic intelligence gathering efforts and the output of our human intelligence network and their informants are being fed directly into the United States “global network” has massive ramifications. Particularly when we consider that the sources of that information may not just be from our overseas/military operations but also from our domestic policing operations. That it could include information obtained not just by our spy agencies and our police agencies – but by their subcontractors, like Thompson and Clark Investigations Limited.
The same U.S. Army intel officer listed in ICWatch also makes reference to “lethal and non-lethal targeting in the COIN efforts of the unit”. COIN stands for U.S. COunterINsurgency doctrine and operations. Counterterrorism is inherently interlinked. In 2015 Michael Gould-Wartofsky, then-PhD candidate at New York University and author of “The new age of Counterinsurgency policing” in The Nation as well as “The Occupiers: The Making of the 99% Movement” was interviewed at length about the crossover between military counterinsurgency operations in areas of operation, and domestic counterterrorism intelligence operations in the West targeted at dissenters:
“Counterinsurgency emerged as a strategy for control and containment of what was seen as enemy forces in foreign combat zones in the 1960s… and has really experienced a revival of sorts, a renaissance, since 9/11… we’ve seen counterinsurgency understood as a struggle for control over contested political space, political territory. We see this counterinsurgency strategy imported back to the homeland, back to domestic uses. So the counterinsurgency framework depends on the establishment and consolidation of control over a population and over a given territory through both military means, that is, security forces, in the case of domestic protests…”
A section of my 2016 piece “Understanding World War III” reported on an official Pentagon strategic planning video released by The Intercept, which revealed that the U.S. Army considers the urban landscape of the world’s major cities to be the ground zero combat zones of the future. This contextualises the militarisation of police (including in New Zealand), who have been supplied with military-grade weapons and training.
As I summarised in the piece: “There is now evidence that stormtrooper-like riot police serving as a domestic army is in fact in alignment with the strategic plans of the Department of Defence.”
The video invokes military Counterinsurgency doctrine “honed in the cities of Iraq and the mountains of Afghanistan“:

In the video, the U.S. Army repeatedly refers to images of militarised riot police as “our soldiers“:
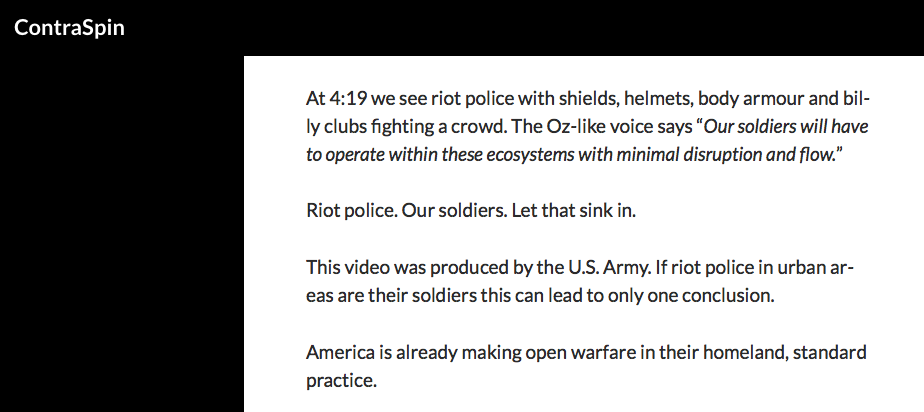
The video states that the Department of Defence must “redefine doctrine and the force in radically new and different ways… The future army will confront a highly sophisticated urban-centric threat…”

The interconnectedness of U.S. law enforcement authorities with those of international partners is further evidenced in yet another ICWatch entry. A “Lead Business Architect” for the “Analytical Framework Program (AFP)” for the “Office of Intelligence and Investigative Liaison” goes into detail about an application he developed in conjunction with the U.S.’s Five Eyes partners – Canada, the United Kingdom, Australia and New Zealand. The express purpose was to address “the multi-year challenge of sharing Personally Identifiable Information (PII) with the Heads of Intelligence (HINT)...”
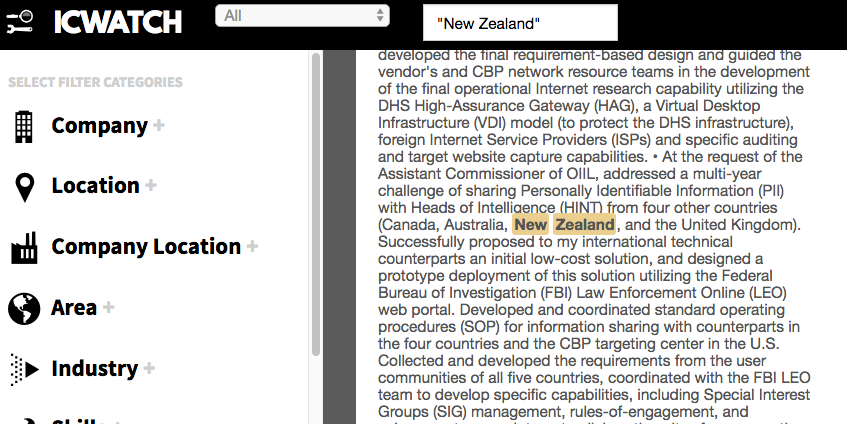
He makes specific reference to having utilised “the Federal Bureau of Investigation (FBI) Law Enforcement Online (LEO) web portal.” The existence of web portals where intelligence agencies across the global network can both request and receive information is further illustrated in the Snowden documents. The NSA has what it calls an “Information Needs Portal” where its customers (which range from law enforcement agencies, to foreign intelligence services, to U.S. government departments and even the U.S. Federal Reserve, which is not a U.S. government body) can submit “Information Needs Requests”.
Just as we Kiwis might log into our internet banking web portals, or our online grocery shopping – these military, law enforcement officers and contractors log onto spy portals to access the information hoovered up by surveillance operations around the world, including in our homeland.
The ability of the agencies of foreign powers, far removed from local surveillance contractors on the ground gathering data on citizens, to access and utilise that data at whim, means that companies like Thompson and Clark Investigations, even if not directly employed by them, effectively become proxy forces for those foreign powers.
From the perspective of the “global network”, it’s free manpower. From the perspective of a target, those surveilling them on the ground become virtually indistinguishable from those watching from inside the global data matrix that increasingly holds influence over all of our lives.
2. The US is Dispatching Our Spies
However, we know thanks to WikiLeaks that the parasitic relationship between U.S. and New Zealand intelligence is not merely passive or voyeuristic.
We now have proof that the U.S. has been dispatching New Zealand human intelligence officers, sending them on overseas missions. And not simply to Afghanistan or Iraq. But in one case, to infiltrate a multitude of political parties contesting the 2012 Presidential elections of an ally – France.
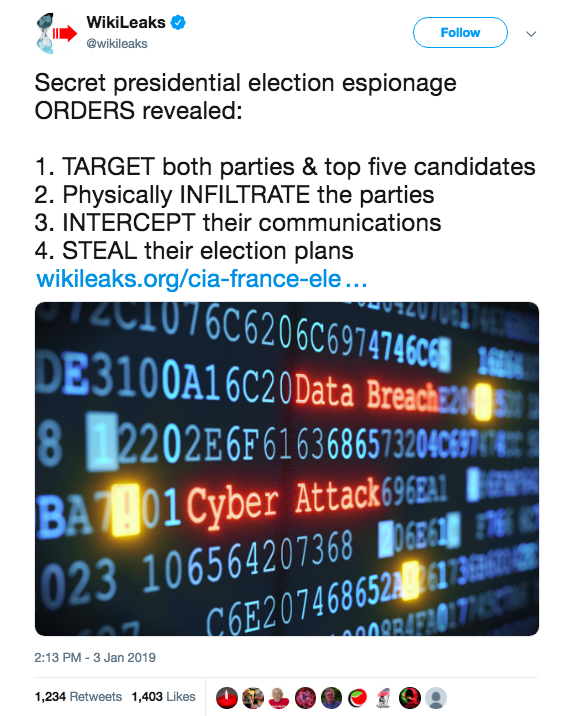
While reported in France, the astonishing revelation was widely ignored by corporate media outlets across the five nations involved in perpetrating the espionage – the U.S., United Kingdom, Canada, Australia and New Zealand.
During the 2017 Internet Party campaign which I led, I used the one and only mainstream media radio interview that I was granted during the entire election season to drive home my concern about the implications of it. I told radio presenter Wallace Chapman:
“In February of this year, WikiLeaks published a document which is from the CIA. In the document, the CIA is dispatching New Zealand human intelligence spies to France, to penetrate political parties in the French Presidential election. So we hear about mass surveillance and about our data being sent to the United States but this is next level. This is the intelligence agency of a foreign power sending dispatch orders to New Zealand foreign intelligence personnel.”
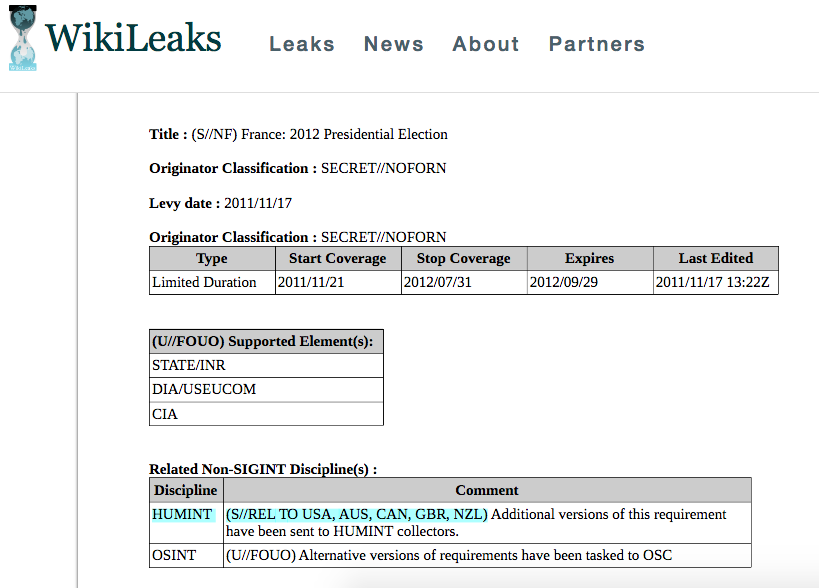
The document itself is fascinating. It is the U.S. version of the dispatch orders, so the subsequent requirements pages (which are worth reading in their entirety, as they outline the specific objectives and types of information the U.S. wants to gather from each political party and even ranks them in order of priority) are largely marked S/NF meaning Secret/No Foreign Nationals – for the eyes of U.S. agencies only. The document states that “additional versions of this requirement have been sent to HUMINT collectors” which seems to suggest that the particulars of dispatch orders from the U.S. vary depending upon who they are issuing them to.
That the UK is named is fascinating. Logically, the UK version of the dispatch orders wouldn’t have disclosed that French political parties’ communications with the UK were part of the brief.
So not only are Five Eyes HUMINT spies being dispatched by a foreign power, they’re doing so for reasons that may not be known to them.
All of the above is a real-world illustration of the dangers of integrating New Zealand’s intelligence services with the “global network” and making our personnel available to ultimately serve the interests of a foreign nation.
A key point in the Cullen-Reddy “Report of the First Independent Review of Intelligence and Security in New Zealand“, undertaken in the wake of the GCSB movement and related spying scandals in New Zealand in the period 2012 onwards, has forever stuck with me. The Hon. Michael Cullen and Dame Patsy Reddy clearly stated:
“Close co-operation on operational matters also creates a risk of some loss of independence, both operationally and potentially also in relation to our intelligence, defence and foreign policy settings…New Zealand’s national interests… do not and cannot exactly coincide with those of any other country, no matter how friendly or close.” (Emphasis added)

A further WikiLeaks release shows that the U.S. weren’t only involving New Zealand in spying on France for political reasons alone. They were ordering us to steal commercial and trade secrets as well.
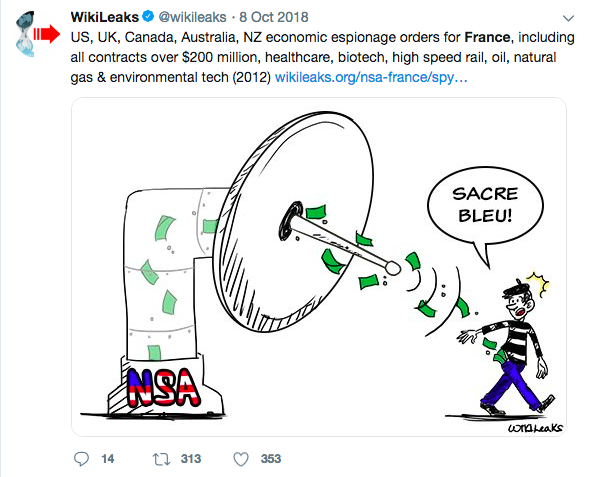
The beneficiaries of the spying (“Supported Elements”) are listed on the orders and include the United States Treasury, the Federal Reserve Board and the U.S. Department of Energy and Infrastructure, to name a few.
Which is all deeply ironic, for both ex-President Barack Obama and ex-Attorney General Eric Holder publicly asserted that the U.S. does not spy for economic reasons or engage in theft of intellectual property.
In May of 2014 The New York Times reported:
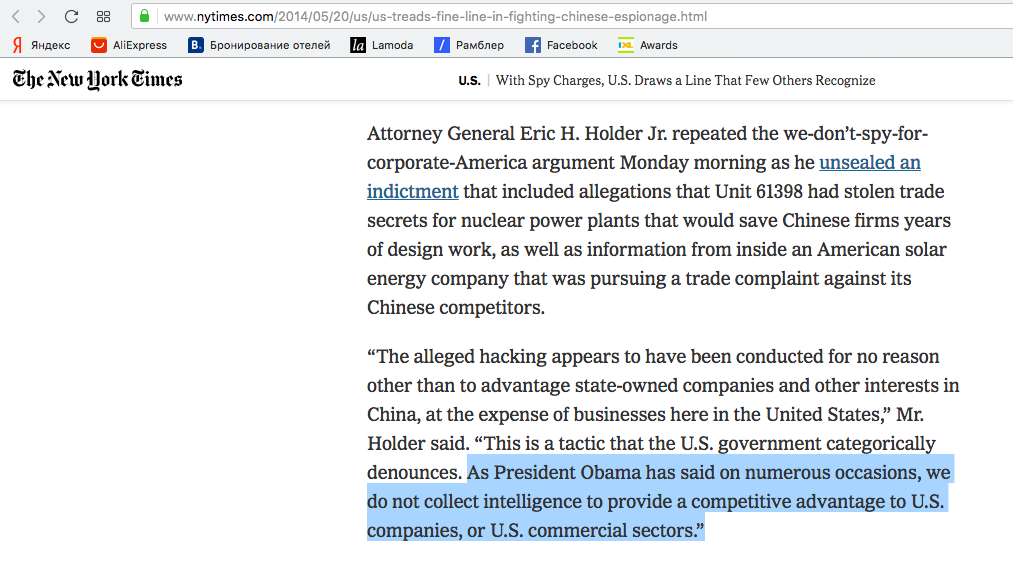
To their credit, the Times went on to detail a number of instances of the U.S. engaging in economic spying, and cited Snowden documents to back it up. Indeed, there are countless files in the Snowden leaks that reference spying under the guise of “Economic Security”. The practice is so rife that the NSA holds an annual “Global Economic Security Day” where they invite members of industry “from across the U.S. Economics and Intelligence Communities” to “enhance their networks” and discuss with them how they can best be served by U.S. intelligence services:
This all gets particularly interesting, where it intersects with national defence legislation. For the great Orwellian twist in this saga, is that the justifications used in law to target citizens, reference the very same activities in which these agencies are themselves engaged.
3. Preying on the Citizenry and Making a Profit
There is no doubt that the U.S. influence on NZ intelligence sharing policy was greatly enhanced by the ascendence of John Key to the office of Prime Minister in 2008. An ICWatch entry indicates that the U.S. was directly involved in drafting “enhanced” information sharing policy for our spy agencies:
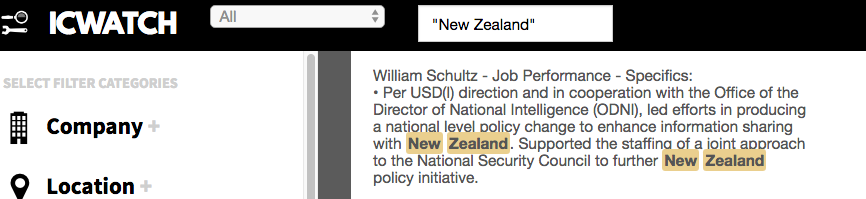
The contractor named in the above screenshot commenced the role in October of 2008, less than a month prior to New Zealand’s 2008 General Election and stayed on through May 2015 so the project would have had to occur within that period.
Within those same years and beyond, New Zealand’s spy agencies have been “enhanced” by more than intelligence sharing – they have been given more money, and increasingly invasive powers, at every turn. This despite them having lurched from scandal to scandal, resulting in the GCSB in particular being permanently etched in the public consciousness and lexicon as little more than a meme, a joke,fit only to be depicted in a cartoon. (Or another cartoon, or another, or another, or another…)
Instead of being punished for the constant revelations of their illegal activity, the GCSB were ultimately rewarded with the granting of retroactive immunity for their crimes. Their incompetence earned them increased budgets and scope. Their non-subjection to any meaningful accountability appears to have been cemented by the release of yet another critical oversight report in 2018. The agency, famous for breaking the law, is apparently breaking the law again. It seems that either they have learned nothing, or perceive that they don’t need to, because they know full well that the true overseers of the “global network” are not in New Zealand at all; are perfectly happy with what they are doing; thus they won’t ever be made to change.
The inclusion of corporate contractors as military personnel under the umbrella Rumsfeld’s “Total Force” has introduced profit motive to intelligence targeting. And so it is, that just as I warned in 2015:
“Due to the for-profit nature of these crimes, which are perpetuated and facilitated by governments and therefore NOT recognised and prosecuted by those governments, the problem is snowballing into a situation where not only protesters and journalists are being stalked and intimidated but even doctors, researchers, scientists, educators, civil servants, and anyone at all who gets in the way of the establishment.”
Civilians are being caught up in the ever-expanding dragnet of the “global network” – the logical outcome of mixing a perpetual growth model with the surveillance industry:
“The thing about the privatisation of spying is that profit requires growth, and growth in this industry means more targets. So it was never going to be a finite thing. It was never going to be, we will just target the activists. Because, if you just target the activists… first of all, they try to diminish the total number of activists and that would mean less profit. So in order to have more profit, they have to constantly expand the sectors of society that they spy on. We’ve seen this in New Zealand. Surveillance cameras used to be for safety in a dark, dingy area. Now they are absolutely everywhere at all times. They have to have ever-increasing saturation of spying in order to make money from it.”– Diary of a Person of Interest
The Anne-Marie Brady case is the most high profile recent example of politically-motivated targeting in New Zealand. Brady’s claims are precisely in step with, and validate past claims myself and other New Zealanders have been making for years. Our experiences foreshadowed hers as if they were mirror images: vehicular sabotage, thefts of electronic equipment, home invasions, surveillance, harassment and other types of psychological targeting methods employed against us by these agencies and their subcontractors.
Dozens if not hundreds more victims would be found if anyone in the NZ media took the leap into the rabbit hole.
I applaud and am relieved for Brady that she has been able to create a bulwark of public support where many other targets are simply written off as crazy or met with a wall of disbelief and silence.
There is a depressing incentive for onlookers to turn the other way when confronted with an issue such as state-level targeting of a citizen. To believe, and to confront the issue, leads to a very scary, very uncomfortable place. To disbelieve is to relieve oneself of any moral obligation to act.
What neither Brady nor her supporters seem aware of or willing to address, however, is that her work didn’t just shine a huge light on China. It focused directly on the same political network that was implicated in the Dirty Politics scandal of 2014. From Brady’s now-famous research paper:
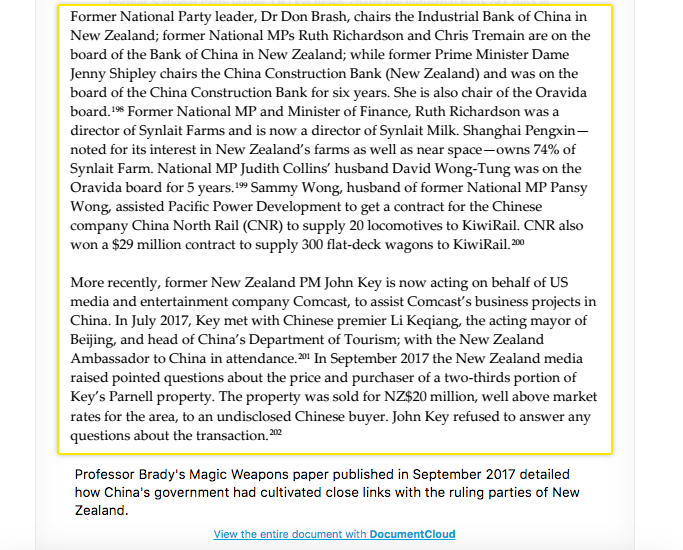
John Key, Judith Collins, David Wong-Tung – these are very familiar names in New Zealand. Brady seems unable to acknowledge that by exposing many questionable connections between China and New Zealand, she is not just exposing the Chinese.
She is exposing New Zealanders. Very well connected New Zealanders.
Recently in an New Zealand Herald interview, Brady complained of being stonewalled when she had tried to supply her information to New Zealand intelligence services ahead of publishing it:
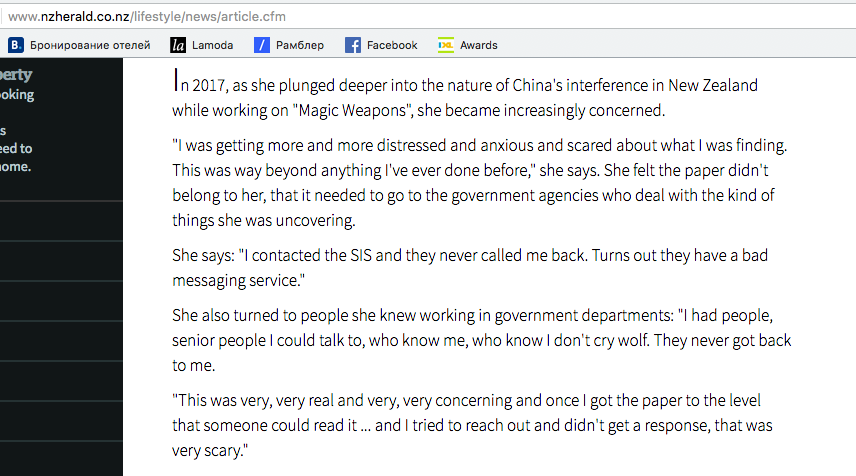
When I made a Privacy Act request to the New Zealand Security Intelligence Service (NZSIS) asking for any information they held on me, they sent me a response stating that I had not supplied required information and that they would neither “confirm nor deny the existence or non-existence” or any data they held on me. I proved to both the NZSIS and the Privacy Commissioner’s Office that I had in fact supplied the requested information and asked for the SIS’s response to be amended accordingly, to no avail.
When I made a Privacy Act request to the GCSB asking explicitly whether I was one of the 80+ New Zealanders known to have been illegally spied on by them they sought an extension to the deadline, stating that they would have to undergo “consultation” before they could respond to me. They eventually responded and said that they would neither confirm nor deny whether I was, citing section 32, and section 27(1)a of the Privacy Act 1993.
I had made my Privacy Act requests in the wake of what I call “the Locke precedent.” Ex Green Party Member of Parliament Keith Locke had also been told by the GCSB that they could neither confirm nor deny whether he was targeted by them. When he took his complaints to the Privacy Commissioner, according to the Otago Daily Times:
After appealing to Privacy Commissioner Marie Shroff, Locke received a letter from Fletcher last week.“I can confirm that you are not amongst the 88 and that GCSB has not conducted surveillance of you.”
When I complained to the Privacy Commissioner about the GCSB having failed to confirm or deny that I was a target, I got a completely different outcome than Locke did.
The Privacy Commission said that they had investigated and that the SIS and GCSB had correctly applied section 32 of the Act and that disclosure to me of whether information was or was not held about me would prejudice sections 27 and 28 of the Privacy Act.
So what on earth are sections 27 and 28 of the Privacy Act?
National security, international relations and trade secrets.
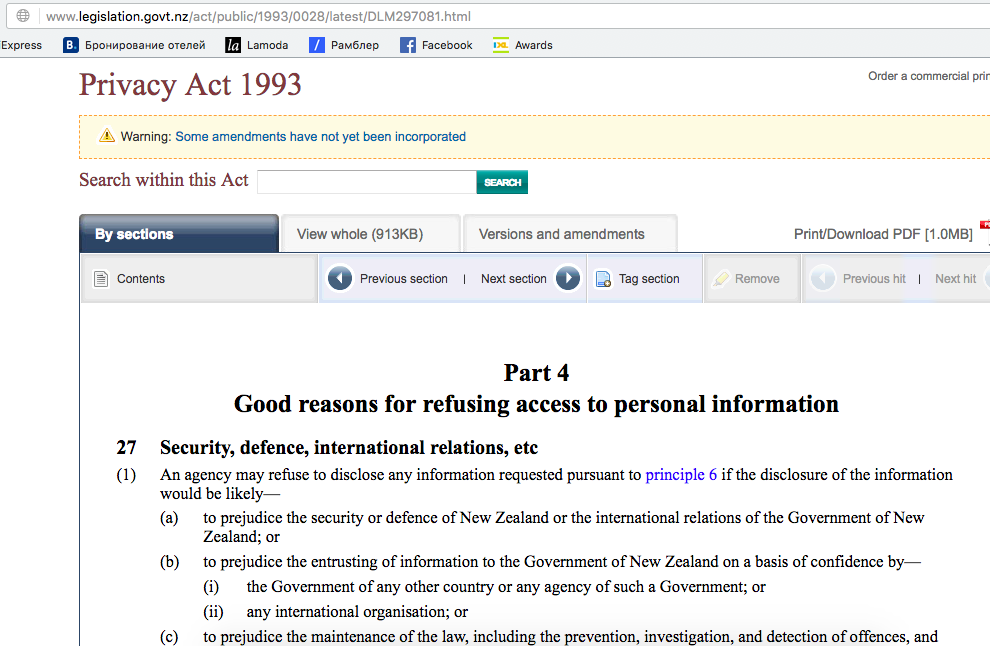
Given the above, it is reasonable to suspect that Brady’s work may have been deemed to be a threat to the international relations of New Zealand – specifically, it’s relationship with China. While China is most likely to be responsible for any targeting of Brady’s contacts on Chinese soil, as she claims has occurred, the NZSIS’s failure to respond to her initial contacts to them, and their long track record of identical methods of political targeting on NZ soil makes it far less likely that China is responsible for Brady’s targeting in New Zealand. As it is the SIS who are now supposedly investigating the targeting of Brady in New Zealand, I’d recommend she start filing her Privacy Act requests now.
The timing of my own Privacy Act requests was not insignificant. In August of 2016, The Intercept in conjunction with television network TVNZ and investigative journalist Nicky Hager revealed the identity of one of the Kiwis who had been then-illegally targeted by the GCSB – Tony Fullman. His case was detailed in the Snowden archive. Sure enough, he was a pro-democracy campaigner, targeted by New Zealand security services under anti-terrorism legislation. His home had been raided, and his passport had been revoked.
Furthermore, it was revealed that the GCSB had sent his personal data to the NSA in Hawaii, where Ed was stationed, in 2012.
It was in 2011 that I first began experiencing politically motivated targeting, and in 2012 that I began seriously investigating the FBI’s activities on New Zealand soil, and the activities of private intelligence contractors. In an April 2012 interview I broke down precisely the types of capabilities of these spies, that a little over a year later, Edward Snowden would conclusively prove had been occurring:
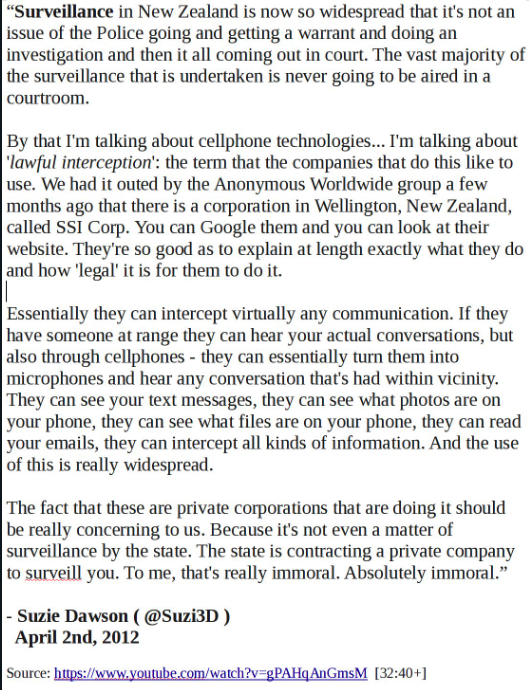
The passage of the 2013 GCSB Bill didn’t whet the appetite of the spy agencies for greater powers. In 2016 the New Zealand government began desperately trying to pass (and eventually did) ‘urgent’ legislation to further enable it to revoke the citizenships of… you guessed it, threats to national security. Simultaneously, they were proposing to redefine the legal definition of what the term “threat to national security’ even meant and were eventually successful. In the words of the Cabinet Paperfrom the Office of the Prime Minister and Cabinet, as a result of their efforts: “The Act now avoids defining the term ‘national security’ in legislation… allowing it to be adaptive to an ever-changing security environment.“
So who gets to decide whether national security is at stake in any given case?
“…it must be determined by the Minister responsible for the relevant intelligence and security agency and a Commissioner of Intelligence Warrants whether something is a matter of national security.”
Determined without a legal definition.
Great Questions
The activities of the New Zealand agencies are carbon copies of what is going on in many other countries around the world – all countries in fact, which are allied with the U.S.: from the integration of their intelligence networks and systems, the appropriation of their human and technical resources by proxy, the mass surveillance of their own and other’s populations, to allowing their assets to be dispatched in the service of a foreign nation.
Their activities have legislative, commercial and constitutional ramifications, as well as impacting negatively upon human rights and democracy as a whole.
Whether the unfolding spy scandal in New Zealand may yet see the resignation of a department head or two, the slap on the wrist of a few police officers, or the shuttering of Thompson & Clark Investigations Limited remains to be seen. From the perspective of the “global network”, all of those people are dispensable and countless others will soon fill their places. It is likely the ink on new contracts is already dried.
But what we need, collectively as a public, is much more than a few firings, or a blacklisted contractor. We need a long, hard, serious think about how it is that entities which we fund and vest powers in, are able to destroy Kiwi lives with such abandon, and the ways in which government agencies, police agencies and corporate entities are pooling their data, their resources and their authority in order to do it.
The only way out of this mess is to reclaim our data sovereignty and assert our national sovereignty.
Of the NZSIS and GCSB we must ask: How they are able to serve the interests of a foreign power above and beyond our own national interest? How are they allowing themselves to be dispatched on missions that they themselves may not even understand the particulars of, where the beneficiary is another nation state and the country being victimised is an ally?
How it is that our national interest ended up being subjugated by the “global network”? Is this is a picture of a future that we want for our country and our communities?
A lot has been learned from the Thompson & Clark scandal but a lot hasn’t been too.
We know that Thompson & Clark spied on multiple political parties – the State Services Commission report refers to both the Mana Movement in 2014 (then allied with the Internet Party of New Zealand of which I am currently party president) and the Green Party having been targets. But we still don’t know the full extent or ramifications of any human intelligence infiltration, data exfiltration, or who Thompson Clark spied on them for.
The LinkedIn page of Gavin Clark, Director of Thompson & Clark Investigations Limited states that one of their key focuses is “Issue-motivated groups (IMGs)” and that they serve “global” customers.
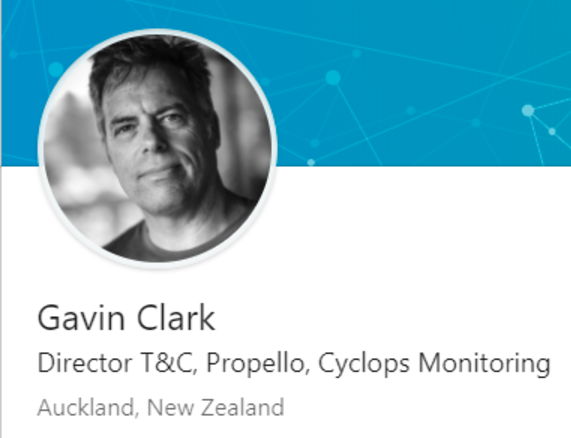
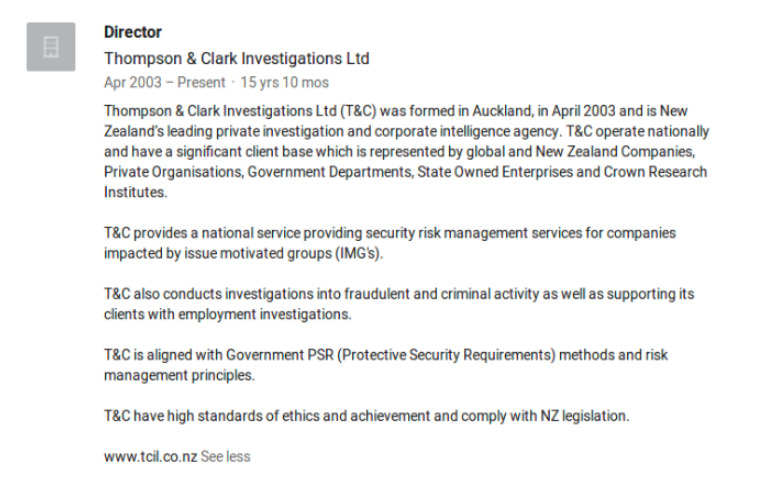
We need to know in whose hands that data ultimately landed.
Peter Dunne has some great questions — in an OpEd for Newsroom he asks:
“Was any information provided, formally or informally, to the intelligence services by Thompson and Clark, and was any information gathered at the behest of the intelligence services?”
His article is titled “Only A First Step In The Data Battle.”
Based on my research, here are what the data flows currently look like:
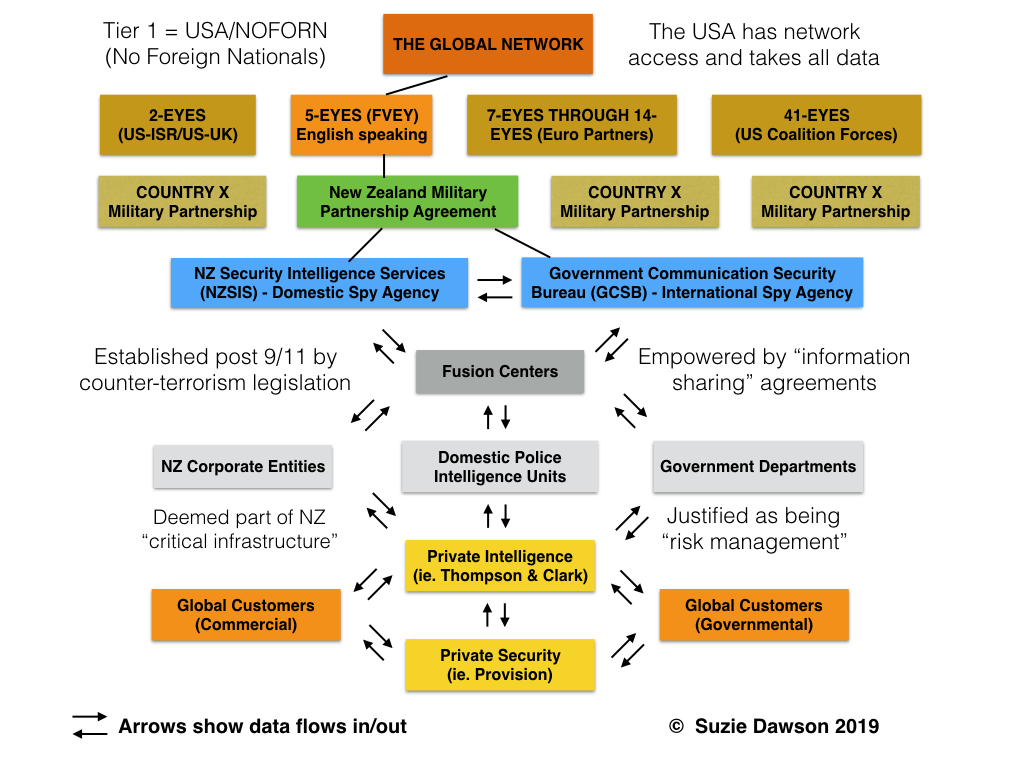
Information collected by private intelligence and security companies like Thompson and Clark is shared with the global and domestic commercial and governmental entities that employ their security, investigatory and “risk management” services, as well as with police intelligence units.
Post 9/11 anti-terrorism legislation deemed a number of corporate industry titans to be a part of the “critical infrastructure” of New Zealand – banks, telcos, transport companies etc. This brought them under the umbrella of the state to enable information sharing between those commercial entities and intelligence agencies.
The information sharing hubs are known as Fusion Centres. They act as a bridge between military, police and corporate customers. They “fuse” commercial, governmental, police and public data sources, analyse the material and feed relevant parts back to interested parties. All of this data is available to the Five Eyes through New Zealand’s military partnership and information sharing agreements with the U.S., such as that earlier referenced in the ICWatch findings.
Anti-money laundering legislation, and a string of Bills and Acts enhancing the powers of the Security Intelligence Services and GCSB in New Zealand, have been fundamentally about empowering this interactivity between commercial, domestic and international.
This is the behemoth Goliath that those of us unlucky enough to be targets find ourselves up against. Far too often targets aren’t ISIS brides, foreign fighters, terrorists, drug traffickers, or even foreign militaries, as the heads of our security services keep claiming. They are instead regular citizens – activists, journalists, dissident academics, researchers, or as we now know even earthquake victims and child abuse survivors. Anyone who pisses off any of the entities in that flow chart can soon find that the data and powers of the collective global network are being utilised against them.
Ex-Green MP Keith Locke has been able to prove that he was targeted since the age of eleven. His victimisation tracks back to 1955, and extends through the new millennium, including three years during which he was a Member of Parliament – a position that is supposed to grant him some immunity from political targeting by security services. As recently as 2013 he was still being referred to as a “threat” in internal NZSIS documents. Why?
Keith writes:
In the SIS documents I was identified as an “internal” threat because I “wish[ed] to see the NZSIS & GCSB abolished or greatly modified”. The documents labelled this a “syndrome”.
Keith Locke isn’t the only New Zealander that wants to see the NZSIS and GCSB abolished or greatly modified. On the above grounds, every person in this crowd would be considered a threat.
I was the top social media influencer for the GCSB movement and filmed the above footage. Our campaign sought to prevent the passage of the 2013 GCSB Bill. My actions were democratic and lawful. The GCSB’s were not.
“Gosh it sounds awfully conspiratorial doesn’t it?” asked Wallace Chapman of me, in our election year Radio NZ interview.
When the conspiracy is written into law, and the evidence is overwhelming, it is no longer a conspiracy theory.
It is a conspiracy fact.
Suzie Dawson is a Kiwi journalist, activist and current President of the Internet Party of New Zealand. She specialises in writing about whistleblowers, intelligence agencies, geopolitics and technology. Her work has been shared by WikiLeaks for the last 5 years running, as well as by other noteworthy figures. Suzie is the organiser of the #Unity4J movement in support of Julian Assange. Journalists who write truth pay a high price to do so. If you respect and value this work, please consider supporting Suzie’s efforts via Bitcoin donation at this link. Thank you! Twitter: @Suzi3D Official Website: Suzi3d.com


